Enhance Productivity and Mitigate Cyberattack Risks with Experienced Cyber Defense Management.
Providing 360º Cyber Defense Technology Solutions to Enable Healthy Cyber Risk Posture, Threat Mitigation Scalability, and Compliance Readiness.
What is your organization’s Dark Web risk?
Click here for your free Dark Web scan!
You will receive your confidential Dark Web scan and a free vCISO consultation on ways to mitigate your risk posture.
Enhance Your Cyber Risk Posture with Leading Cyber Defense Management and Consulting.
As cyber threats to businesses and member organizations continue to grow exponentially, it is important to have access to Security leadership with experience and knowledge in navigating the complexities of the ever-evolving threats against organizations and business systems. Our TrueSecure virtual CISO (vCISO) program provides the specialized technical knowledge and corporate governance experience to help build not only a strong cyber security foundation but also the agility to prevent, detect and mitigate evolving threats to your organizational staff and systems. As your vCISO, we will focus on the high-level cybersecurity needs of the organization: cyber awareness and phishing training, security policies, guidelines, compliance standards (ex. HIPAA, PCI, GLBA, SOX, FERPA, SSAE16 | SOC Reports), and 24x7x365 security operations center support.
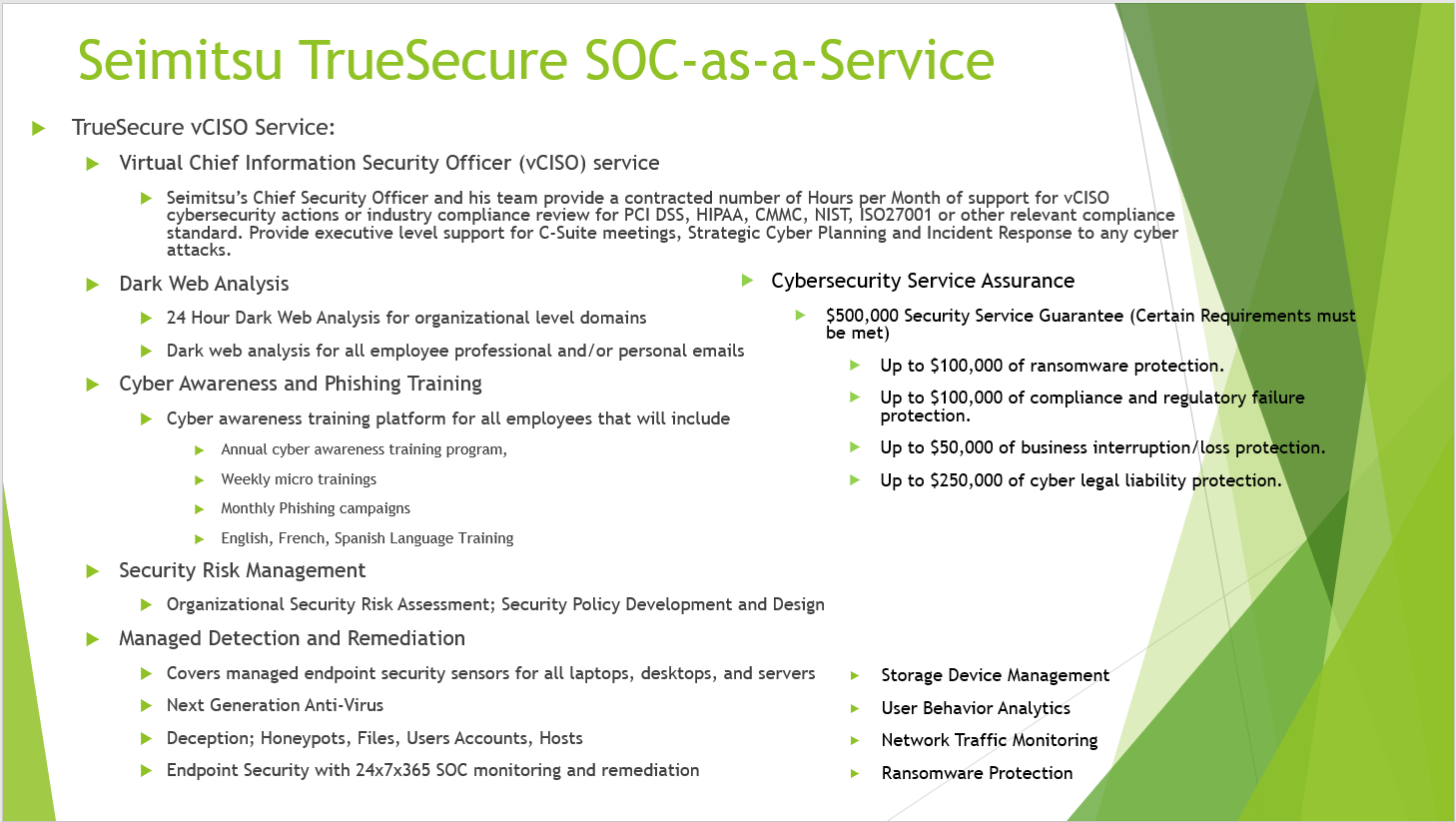
TrueSecure vCISO Security Solutions
Our breach protection platform coupled with other best-in-class award-winning tools provides an enterprise-level cybersecurity stack that is affordable for small to medium businesses. We design and implement a program that provides annual cyber awareness training and ongoing weekly micro-training activities for all staff. With scammers seeking to gain access to organizations through email phishing attacks, we also run phishing campaigns to train staff on the dangers of email attacks. Our policy portal has all the security policies you need to be HIPAA and PCI-compliant. As your vCISO, we will conduct ongoing security risk assessments for the organization to maintain awareness of what technology, personnel, and policy changes should be made to enhance the organization’s cyber risk posture. Our breach protection platform is coupled with the best-in-class extended detection and mediation techniques available to secure your laptops, desktops, and servers running Windows. Mac, or Linux OS.
Our vCISO solutions also provide your organization with our TrueSecure $500,000 Security Service Assurance. Seimitsu will provide no-cost remediation to a cyber attack under qualifying conditions as per the following cybersecurity controls checklist in place for your organization:
Cybersecurity controls checklist for TrueSecure Assurance
Threat monitoring for ransomware/ business email compromise is continuous
Data backup & Encryption of data at rest
Patching cadence followed - within 60 days of release
Multi-factor authentication is on all employee email accounts
Client verifies / documents any out-of-band wire requests or changes in routing instructions on invoices.
TrueSecure Service Assurance Coverage
Up to $100,000 of ransomware protection.
Up to $100,000 of compliance and regulatory failure protection.
Up to $50,000 of business interruption/loss protection.
Up to $250,000 of cyber legal liability protection.
Do you also need Cyber Insurance? We do not sell insurance but we have developed industry relationships that allow us to get your organization quotes for cyber insurance that are between 20% and 40% lower on average.
Get a cyber insurance quote on our referral portal here.
The following components are part of our complete TrueSecure vCISO offering.
Security Risk Assessment
We identify human and technological vulnerabilities and their related risks. Based on NIST standards, our Security Risk Assessment (SRA) assesses your administrative, physical, and technical vulnerabilities; identifies the associated risks, and provides recommendations for improvement
Cyber Breach Incident Response
Are you actively involved in a cyberattack? Contact us immediately for Incident Response support. Seimitsu’s TrueSecure Incident Response Team will coordinate with your onsite team for in-person or remote collaboration for remediation of the ongoing attack on your network. We can deploy security across your network to 5000 endpoints in under one hour and begin remediating the active attack.
Our lightweight extended detection and remediation (XDR) agent will seamlessly integrate Next-Generation AV (NGAV), Endpoint Detection and Response (EDR), User Behavioral Analytics (UBA), Network Detection and Response (NDR), and Deception powered by the Cynet360 engine.
TrueSecure Security Operations Center
The TrueSecure Security Operations Center (SOC) provides 24/7 support capabilities and is available for a host for SOC services that include Incident Response, Digital Forensics Analysis, Cyber Crime Analysis support to LEO’s, Social Media Analytics, Big Data Analytics, Cybersecurity Audits, and security consulting.
Our Breach Protection Platform (BPP) allows us to deliver you many security features that you would have to pay for separately and for much more from other organizations. It lets us help your organization build your workforce into strong frontline cyber-aware users that can help stop attacks. It allows us to conduct 24 hour Dark web monitoring that looks for your organizational data in dark web data breaches, provide annual cyber awareness training, automated phishing campaigns, a security policy portal that we create 10 or more security policies for your organization aligned with the compliance requirements of your industry, and security risk assessments validated by a third-party security auditor. It also gives your employees a security score similar to a credit score that shows who is taking security seriously in your organization and who should be nudged along to do better.
Take a Look Inside Our TrueSecure Next Generation Anti-Virus and 24x7x365 Endpoint Security Protection! Managed detection and remediation are done utilizing our partnership with Cynet. Our security team works in conjunction with your IT or Security team or functions as your security team to monitor all activities on your laptops, desktops, and servers. We monitor your network 24x7x365 with a sensor that provides Next-Generation Antivirus (which not only looks at vulnerability repositories but the live actions of files), network traffic analysis, user behavior analytics (when do users log on, to what systems, what times of day, and assess if these are within normal actions), devices analytics ( has something been connected to your endpoint that is not normal), Deception, threat hunting and much more.
Our vCISO program is unmatched for price and services delivered.

Are You Enabling Your Team to Operate at the Highest Level of Security?
Hiring an in-house security team is expensive, distracting and inefficient. For flexible cybersecurity management that’s available when you need it, start with our Seimitsu vCISO solutions today.
Would You Like to Partner With Us To Provide Managed Security?
Better cybersecurity management starts with Seimitsu.
Click below to get in touch with our team of cybersecurity analysts.